SAP User Role Access Rights for zapAudit and zapCash
Overview of the necessary authorizations to enable Remote Function Call (RFC) access to your SAP System
To utilize zapAudit or zapCash seamlessly, specific SAP user role access rights are essential. This guide provides a comprehensive overview of the necessary authorizations to enable Remote Function Call (RFC) access to your SAP System. The SAP user requires full BBP_RFC_READ_TABLE access authorizations for optimal functionality.
You can also use a system user (USTYP B in USR02) instead of a dialog user (USTYP A in USR02).
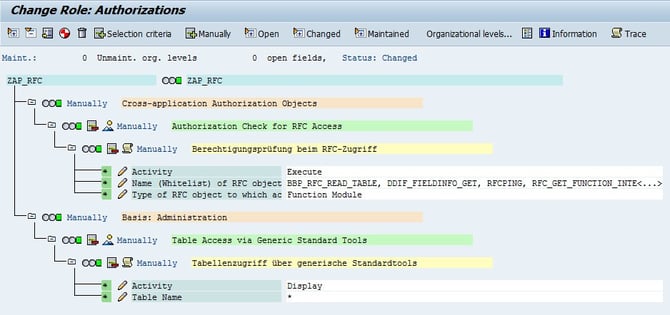
Mandatory Access Rights
-
- S_RFC Authorization Object:
- Activity (ACTVT):
- Execute (16)
- Name of RFC-Objekts (RFC_NAME):
- BBP_RFC_READ_TABLE
- DDIF_FIELDINFO_GET
- RFCPING
- RFC_GET_FUNCTION_INTERFACE
- RFC_READ_TABLE
- STFC_CONNECTION
- SO_DOCUMENT_READ_API1
- ALINK_RFC_TABLE_GET
- Activity (ACTVT):
-
- Type of RFC-Objects (RFC_TYPE):
- Function Module (FUNC)
- Type of RFC-Objects (RFC_TYPE):
- S_TABU_NAM Authorization Object:
- Activity (ACTVT):
- Display (03)
- Table Name (TABLE): *
- Activity (ACTVT):
- S_RFC Authorization Object:
If “*” cannot be assigned to the authorization object “S_TABU_NAM,” the individual tables can also be specified from the data scope.
SO_DOCUMENT_READ_API1 and ALINK_RFC_TABLE_GET is required for attachment download.
Additional Table Authorizations
For manual containment of SAP tables, enter the following tables in the "Table Name (TABLE)" field:
| DD17S, T000, T001, T001A, T009, T009B, T001K, DD07T, NRIV, T001L, T001W, T003, T003T, T005, T005T, T007S, T008, T008T, T011, T011T, T014, T023T, T030K, T030W, T041C, T041CT, T043, T052, T052U, T074T, T077S, T077Z, T093, T093C, T093T, T100, T134T, T156, T156T, T159L, T161, T161T, T163, T173, T173T, T685, T685T, T880, T881, TABW, TABWT, TBSL, TBSLT, TCURC, TCURT, TCURX, TCURF, TCURP, TCURR, TCURV, TPFID, TSTCT, TTYP, TVAK, TVAKT, TVFS, TVFST, TVLK, TVLKT, BKPF, REGUV, BSEG, BSET, FAGL_011FC, FAGL_011PC, FAGL_011QT, FAGL_011SC, FAGL_011TC, FAGL_011VC, FAGL_011ZC, REGUH, REGUP, SKA1, SKAT, SKB1, EKKO, EKPO, EBAN, EKBE, TVKO, VBAK, VBRK, LIKP, LIPS, VBAP, VBRP, USR02, USR40, UST04, ANEP, ANLA, ANLB, ANLBZA, ANLC, ANLH, ANLZ, ANKA, ANKT, MARA, MKPF, MSEG, MAKT, MBEW, TDG41, KNB1, LFB1, KNA1, KNBK, LFA1, LFBK, KNKK, CDPOS, CDHDR,TCDOB, TCDOBT, TIBAN, KNAS, SRGBTBREL, TOA01, TOA02, TOA03, DD02T, DD03L, DD04T, TKA02, LFAS,TOASP,BSEC,GLT0,T012K,T042I,FAGLFLEXA,FAGLFLEXT,BUT000,CVERS,CVERS_ACT,CVI_CUST_LINK,UKMBP_CMS_SGM,VBFA,GLT0 |
Setting Up User Role in SAP
- Use transaction SU01.
- Select the SAP user to edit.
- Navigate to the 'Roles' tab.
- Activate 'Edit' mode (Shift + F7) and select 'Change Role' or double-click the role.
- Go to the 'Authorizations' tab.
- Click 'Change Authorization Data,' possibly pressing Shift + F7 to activate editing.
- Edit function objects as required
Additional Information:
-
- If S_TABU_NAM is unavailable, use S_TABU_DIS with activity 'Display' and '*' for the table authorization group.
- If FUNC is unavailable, use the function group (FUGR) with the following objects:
- BBPB for BBP_RFC_READ_TABLE
- RFC1 for RFC_GET_FUNCTION_INTERFACE
- SYST for RFCPING
- SDIFRUNTIME for DDIF_FIELDINFO_GET
- SDTX for RFC_READ_TABLE
Note:
- If 'Single Sign-On' with 'Active Directory' is activated, the user must still be able to log on to SAP with a password.